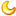扫描时间
2007-3-17 14:20:30 - 2007-3-17 14:32:42
检测结果
存活主机 1
漏洞数量 0
警告数量 1
提示数量 14
主机列表
主机 检测结果
www.bc-cn.net 发现安全警告
主机摘要 - OS: Unknown OS; PORT/TCP: 21, 80, 1433, 3389, 6001
[返回顶部]
主机分析: www.bc-cn.net
主机地址 端口/服务 服务漏洞
www.bc-cn.net x11 X Window System (6001/tcp) 发现安全提示
www.bc-cn.net www (80/tcp) 发现安全提示
www.bc-cn.net ftp (21/tcp) 发现安全提示
www.bc-cn.net ms-sql-s (1433/tcp) 发现安全提示
www.bc-cn.net Windows Terminal Services (3389/tcp) 发现安全提示
www.bc-cn.net msrdp (3389/tcp) 发现安全警告
www.bc-cn.net mssql (1433/tcp) 发现安全提示
www.bc-cn.net tcp 发现安全提示
安全漏洞及解决方案: www.bc-cn.net
类型 端口/服务 安全漏洞及解决方案
提示 x11 X Window System (6001/tcp) 开放服务
"x11 X Window System"服务可能运行于该端口.
NESSUS_ID : 10330
提示 www (80/tcp) 开放服务
"WEB"服务运行于该端口
BANNER信息 :
HTTP/1.1 302 Object moved
Connection: close
Date: Sat, 17 Mar 2007 06:20:54 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
Location: http://blog.bc-cn.net/blog.asp?name=222.43.120.75
Content-Length: 170
Content-Type: text/html
Set-Cookie: ASPSESSIONIDACRSCBTR=DDONOJIBFFGGLFMPNBJHLJHB
path=/
Cache-control: private
<head><title>Object moved</title></head>
<body><h1>Object Moved</h1>This object may be found <a HREF="http://blog.bc-cn.net/blog.asp?name=222
NESSUS_ID : 10330
提示 www (80/tcp) 目录扫描器
该插件试图确认远程主机上存在的各普通目录
___________________________________________________________________
The following directories were discovered:
/admin, /cert, /code, /guestbook, /images, /inc, /info, /js, /temp, /xml
While this is not, in and of itself, a bug, you should manually inspect
these directories to ensure that they are in compliance with company
security standards
NESSUS_ID : 11032
Other references : OWASP:OWASP-CM-006
提示 www (80/tcp) HTTP 服务器类型及版本
发现 HTTP 服务器的类型及版本号.
解决方案: 配置服务器经常更改名称,如:'Wintendo httpD w/Dotmatrix display'
确保移除类似 apache_pb.gif 带有 Apache 的通用标志, 可以设定 'ServerTokens Prod' 为受限
该信息来源于服务器本身的响应首部.
风险等级 : 低
___________________________________________________________________
The remote web server type is :
Microsoft-IIS/6.0
NESSUS_ID : 10107
提示 www (80/tcp) Find if IIS server allows BASIC and/or NTLM authentication
The remote host appears to be running a version of IIS which allows remote
users to determine which authentication schemes are required for confidential
webpages.
Specifically, the following methods are enabled on the remote webserver:
- IIS NTLM authentication is enabled
Solution : None at this time
Risk factor : Low
CVE_ID : CAN-2002-0419
BUGTRAQ_ID : 4235
NESSUS_ID : 11871
提示 ftp (21/tcp) 开放服务
"FTP"服务运行于该端口.
BANNER信息 :
220 Serv-U FTP Server v6.3 for WinSock ready...
NESSUS_ID : 10330
提示 ftp (21/tcp) FTP服务的版本和类型
通过登陆目标服务器并经过缓冲器接收可查出FTP服务的类型和版本。这些注册过的标识信息将给予潜在的攻击者们关于他们要攻击的系统的额外信息。版本和类型会在可能的地方被泄露。
解决方案:将这些注册过的标识信息转变为普通类别的信息。。
风险等级:低
___________________________________________________________________
Remote FTP server banner :
220 Serv-U FTP Server v6.3 for WinSock ready...
NESSUS_ID : 10092
提示 ms-sql-s (1433/tcp) 开放服务
"ms-sql-s"服务可能运行于该端口.
NESSUS_ID : 10330
提示 ms-sql-s (1433/tcp) Microsoft SQL TCP/IP listener is running
Microsoft SQL server is running on this port.
You should never let any unauthorized users establish
connections to this service.
Solution: Block this port from outside communication
Risk factor : Medium
CVE_ID : CAN-1999-0652
NESSUS_ID : 10144
提示 Windows Terminal Services (3389/tcp) 开放服务
"Windows Terminal Services"服务可能运行于该端口.
NESSUS_ID : 10330
提示 Windows Terminal Services (3389/tcp) Windows Terminal Service Enabled
The Terminal Services are enabled on the remote host.
Terminal Services allow a Windows user to remotely obtain
a graphical login (and therefore act as a local user on the
remote host).
If an attacker gains a valid login and password, he may
be able to use this service to gain further access
on the remote host. An attacker may also use this service
to mount a dictionnary attack against the remote host to try
to log in remotely.
Note that RDP (the Remote Desktop Protocol) is vulnerable
to Man-in-the-middle attacks, making it easy for attackers to
steal the credentials of legitimates users by impersonating the
Windows server.
Solution : Disable the Terminal Services if you do not use them, and
do not allow this service to run across the internet
Risk factor : Low
BUGTRAQ_ID : 3099, 7258
NESSUS_ID : 10940
警告 msrdp (3389/tcp) Microsoft Windows Remote Desktop Protocol Server Private Key Disclosure Vulnerability
The remote version of Remote Desktop Protocol Server (Terminal Service) is
vulnerable to a man in the middle attack.
An attacker may exploit this flaw to decrypt communications between client
and server and obtain sensitive information (passwords, ...).
See Also : http://www.oxid.it/downloads/rdp-gbu.pdf
Solution : None at this time.
Risk factor : Medium
CVE_ID : CAN-2005-1794
BUGTRAQ_ID : 13818
NESSUS_ID : 18405
提示 mssql (1433/tcp) Microsoft SQL TCP/IP listener is running
Microsoft SQL server is running on this port.
You should never let any unauthorized users establish
connections to this service.
Solution: Block this port from outside communication
Risk factor : Medium
CVE_ID : CAN-1999-0652
NESSUS_ID : 10144
提示 mssql (1433/tcp) Microsoft SQL TCP/IP listener is running
Microsoft SQL server is running on this port.
You should never let any unauthorized users establish
connections to this service.
Solution: Block this port from outside communication
Risk factor : Medium
CVE_ID : CAN-1999-0652
NESSUS_ID : 10144
提示 tcp 查找主机的FQDN
如果主机可以被解析得到FQDN,这个插件将在报告中显示主机的FQDN。
这是正常的信息泄露。
风险等级:无
___________________________________________________________________
222.43.120.75 resolves as www.bc-cn.net.
NESSUS_ID : 12053
呵呵 看来静的安全工作搞的还不错,老K是不是有点麻烦了?
另外一份BBS的漏洞页面扫描报告 如需要 跟贴 奉上 
[UserName=Knocker]
又查了查
发现了这些~~
http://blog.bc-cn.net/login.asp
http://blog.bc-cn.net/count.asp
http://blog.bc-cn.net/login.asp
http://blog.bc-cn.net/admin_edit.asp
http://blog.bc-cn.net/upload.asp
http://blog.bc-cn.net/config.asp
http://bbs.bc-cn.net/admin_login.asp
http://bbs.bc-cn.net/login.asp
http://bbs.bc-cn.net/admin_login.asp
http://bbs.bc-cn.net/login.asp
http://bbs.bc-cn.net/admin_login.asp
[此贴子已经被作者于2007-3-19 17:51:35编辑过]